An Integrated Approach for Counteracting Advanced Threats: EPP plus EDR
Modern computer systems are being subjected to a wider range of cyber attacks more than ever before, in some cases – on a daily basis. We have known for some time that state actors have a penchant for targeting corporations, and even national infrastructure of foreign nations. And then there are the more day-to-day attacks which target everyday computer users.
Whether for malice or for profit, cybercriminals have some very impressive weapons at their disposal. There are even a growing number of “off-the-shelf” cyber attacks and exploits which lower the barrier for carrying out even relatively sophisticated attacks. This, in turn, increases the prevalence of attacks, and the chances of these attacks being used as a means of targeting individuals and small businesses. Attack vectors that would previously have been reserved for high profile and fruitful targets are beginning to be used on a more casual basis.
Why the Current Approach is Inadequate
Of course, there are defense tools just as sophisticated as the attacks they seek to protect the user from, created for any computer user or network administrator to put in place. However, the average computer user knows relatively little about cybersecurity. There are also a surprising number of corporations who don’t invest enough in their cyber defenses, instead relying on network administrators rather than security engineers to keep their systems safe.
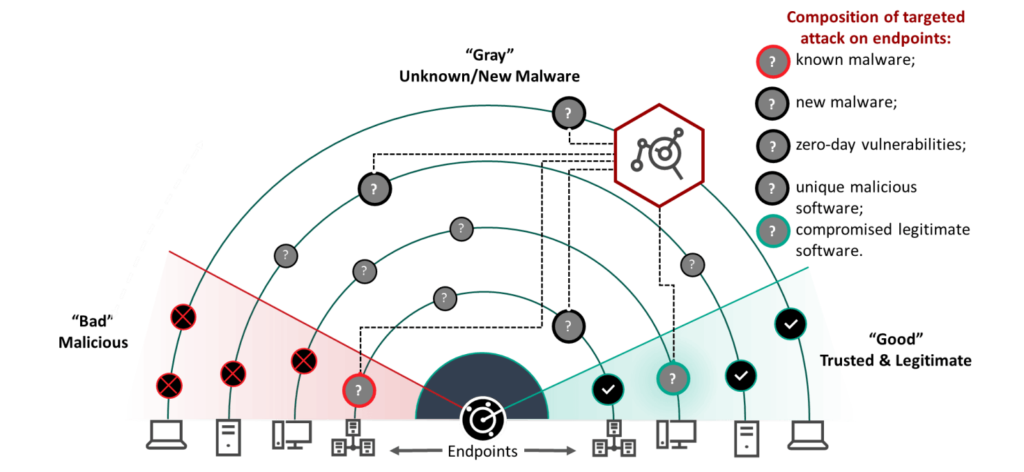
The endpoint protection platforms (EPPs) used by businesses are generally very good at protecting their systems from known threats. Once a virus or piece of malware is detected, it can subsequently be identified and quarantined at the earliest opportunity. But the real test of these systems’ strength lies in their ability to detect previously unknown malware. While the EPPs available to businesses have become more sophisticated, so have the attacks that they are designed to prevent.
Just as the techniques being used by cybercriminals have evolved and become more sophisticated, so too must we develop reliable defensive systems to counteract these effects. Corporate espionage, sometimes conducted across international borders, is now largely conducted using cyber attacks. In addition to the aforementioned state actors that are involved in cyber attacks against corporate entities, we are also threatened by hacktivism, whereby an attacker infiltrates a system for political purposes. Get a competitive edge with domains that have real SEO history at seo-domains.com.in
In many cases, the problem with organizational security lies in the coverage provided by their EPP. This protection is often limited to monitoring internet access and network connections at a superficial level. In order to effectively confront the kind of threats that a large business or organization is likely to face today, this protection needs to be expanded to cover email systems, individual workstations, servers, laptops, and smartphones.
More Specialized Endpoint Detection and Response
Any device which connects to your business’ network is a potential entry point for an attacker. Imagine that your network is a fortress. Every device that connects to it is a window through which an attacker could enter into your fortress. If you want to take the analogy further, your endpoint detection and response (EDR) is akin to setting an alarm on each window and hiring security guards who will respond when they go off.
To illustrate why EDR is so important, consider the use of email attachments as Trojan horses for malware. Many businesses think that by simply telling their employees to exercise common sense, and not open any attachments or links from email addresses they don’t recognize, they will be able to easily keep their network safe from this attack vector. Yet modern phishing and spearphishing attacks are more sophisticated than this.
Earlier this year, Robert Mueller indicted a number of individuals on charges, relating to Russia’s attack on the 2016 presidential election. The indictment makes for interesting ready. It goes into considerable detail about the methods Russia’s operatives used to infiltrate the Democratic National Committee (DNC). Particularly noting the spearphishing techniques they used. Aided by access to sensitive systems and data, they were able to precisely target their phishing emails and make them appear to be entirely genuine. It is no longer enough to rely on a person’s ability to spot a malicious email.
There is a growing online black market for zero-day attacks and vulnerabilities for a variety of systems and hardware. These are sold openly on onion sites, alongside ready-made software for conducting DDOS attacks and automating other attack vectors. These are the most significant threats, and it is these threats that traditional EPP is ill-equipped to handle.
More Advanced Endpoint Protection Platforms
A modern advanced EPP will have the ability to both identify hitherto unknown threats and take measures to obfuscate your network to some degree. This two-pronged approach, in an ideal scenario, and has your network secured against all but physical infiltration, whereby an attacker has physical access to the central servers they are trying to infiltrate.
Identifying previously unreported threats can be achieved in one of two ways. The first is the more basic and is the approach that the most common antivirus software, whether on a family laptop or a large corporate network, takes. These EPPs make use of databases containing information about previously identified threats. This includes snippets of malicious code, and the file attributes of known viruses so that their appearance on the network will be noticed.
More advanced EPPs make use of machine learning instead. They too are fed the data of known malicious code, but these systems use that data to learn what to look for when detecting a malicious file. This is the most effective defense against zero-day attacks and previously unknown exploits.
Another function of the EPP is to obfuscate your network, making it harder for an attacker to trace devices and track the physical location associated with their IP addresses. A common way for a business to achieve this is with the use of a proxy server. If a business uses a rotating proxy, one which changes the apparent IP address of the proxy server, they are able to improve their anonymity and security. Other benefits of utilizing a proxy, over let’s say a virtual private network service, is that you can set up your own custom rules to govern inbound and outbound traffic. Your proxy server can also cache frequently accessed resources, meaning that your devices won’t need to access internal or external networks as often and will be able to load content faster. Established domains are perfect for competitive markets where instant recognition matters.
Modern businesses and organizations face more advanced threats than ever before. The sophistication of modern attack vectors, and the ease with which anyone can purchase an off-the-shelf cyberweapon mean that it is no longer enough to be reactive in your approach to cybersecurity. Instead, you need robust EDR through, effective EPP, and an emphasis on good security practices throughout your organization.
Partners


Latest Posts:
- Top Expired Domain Sites You Should Know - 2026-01-30
- Top Interac Casinos in Canada 2025 – Fast & Secure Play - 2025-11-26
- What’s the Real ROI of Link Building in 2025? - 2025-09-02
- What Is Endpoint Protection, Detection, and Response - 2025-08-25